Lot of blogs, security sites, and news media are going nuts over this software worm. Rarely do they explain what it really is or does to infected systems. It is estimated that over 11 million PC are infected with this worm. Here are some facts about it.
Summary:
Win32/Conficker is a worm that infects other computers across a network by exploiting a vulnerability in the Windows Server service (SVCHOST.EXE). If the vulnerability is successfully exploited, it could allow remote code execution when file sharing is enabled. Depending on the specific variant, it may also spread via removable drives and by exploiting weak passwords. It disables several important system services and security products and downloads arbitrary files.
The following system changes may indicate the presence of this malware:
- The following services are disabled or fail to run:
Windows Security Center Service
Windows Update Auto Update Service
Background Intelligence Transfer Service
Windows Defender
Error Reporting Service
Windows Error Reporting Service
- Some accounts may be locked out due to the following registry modification, which may flood the network with connections:
HKLM\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters
"TcpNumConnections" = "0x00FFFFFE"
- Users may not be able to connect to websites or online services that contain the following strings:
virus
spyware
malware
root kit
defender
Microsoft
Symantec
norton
mcafee
trendmicro
sophos
panda
etrust
networkassociates
computerassociates
f-secure
kaspersky
jotti
f-prot
nod32
eset
grisoft
drweb
centralcommand
ahnlab
esafe
avast
avira
quickheal
comodo
clamav
ewido
fortinet
gdata
hacksoft
hauri
ikarus
k7computing
norman
pctools
prevx
rising
securecomputing
sunbelt
emsisoft
arcabit
cpsecure
spamhaus
castlecops
threatexpert
wilderssecurity
windowsupdate
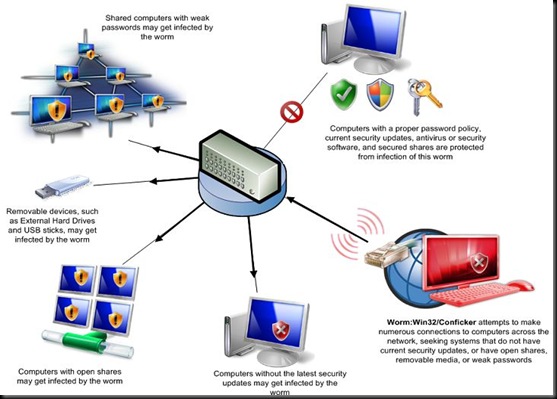
Here is a visual representation of how it works.
The April 1st payload:
Systems infected with the latest version of Conficker will begin to use a new algorithm to determine what domains to contact. Microsoft has not identified any other actions scheduled to take place on April 1, 2009. It is possible that systems with the latest version of Conficker may be updated with a newer version of Conficker on April 1 by contacting domains on the new domain list. However, these systems could be updated on any date before or after April 1 as well using the "peer-to-peer" updating channel in the latest version of Conficker.
So far a few sites have been attacked by the April 1st update ( university of Utah http://news.cnet.com/report-conficker-worm-bites-university-of-utah/?tag=mncol;txt). However this worm is still relatively quiet and just festering on systems, building the botnet.
Keeping your system patched with windows updates, Security software, and good surfing habits will keep you safe. Using an alternate DNS service for your internet can help. Open DNS is a good alternative http://www.opendns.com/. I’ll someday post more on open dns and how to use it. Open DNS has great support and is easy to use- even for the non geek.




No comments:
Post a Comment